Installing Nginx Free HTTPS Certificate on Ubuntu Linux
This tutorial will show you all the steps required to configure Nginx Server Blocks on Ubuntu Linux.
Nginx Server Blocks is very much the same as Apache Virtual host feature.
This tutorial was tested on Ubuntu 18.04.
1. Install Nginx on Ubuntu Linux
Use the Ubuntu APT command to install the Nginx server.
# apt-get update
# apt-get install nginx
Restart the Nginx web server manually.
# service nginx restart
# service nginx status
Verify the Nginx service status.
● nginx.service – A high performance web server and a reverse proxy server
Loaded: loaded (/lib/systemd/system/nginx.service; enabled; vendor preset: enabled)
Active: active (running) since Sat 2018-12-29 04:29:22 UTC; 1h 17min ago
Docs: man:nginx(8)
Process: 2233 ExecStart=/usr/sbin/nginx -g daemon on; master_process on; (code=exited, status
Process: 2221 ExecStartPre=/usr/sbin/nginx -t -q -g daemon on; master_process on; (code=exite
Main PID: 2238 (nginx)
Tasks: 2 (limit: 1152)
CGroup: /system.slice/nginx.service
├─2238 nginx: master process /usr/sbin/nginx -g daemon on; master_process on;
└─2239 nginx: worker process
You finished the Nginx Web server installation on Ubuntu Linux.
2. Add PHP support to Nginx
Nginx needs an external program to add PHP support.
Use the Ubuntu APT command to install the PHP required packages.
# apt-get update
# apt-get install php7.2-fpm
Optional. Use the following command to install the most used PHP modules.
# apt-get install php7.2-xml php7.2-curl php7.2-gd php7.2-mbstring php7.2-mysql
# apt-get install php7.2-bz2 php7.2-zip php7.2-json php7.2-readline
Find the location of the PHP configuration file on your system.
Edit the php.ini configuration file.
# updatedb
# locate php.ini
# vi /etc/php/7.2/fpm/php.ini
Your PHP version may not be the same as ours.
Your PHP configuration file location may not be the same as ours.
Here is the file with our configuration.
file_uploads = On
max_execution_time = 300
memory_limit = 256M
post_max_size = 32M
max_input_time = 60
max_input_vars = 4440
upload_max_filesize = 32M
Edit the Nginx default website configuration file.
# vi /etc/nginx/sites-available/default
Here is the original file, before our configuration.
server {
listen 80 default_server;
listen [::]:80 default_server;
root /var/www/html;
index index.html index.htm index.nginx-debian.html;
server_name _;
location / {
try_files $uri $uri/ =404;
}
}
Here is the new file with our configuration.
server {
listen 80 default_server;
listen [::]:80 default_server;
root /var/www/html;
index index.php index.html index.htm;
server_name _;
location / {
try_files $uri $uri/ =404;
}
location ~ .php$ {
include snippets/fastcgi-php.conf;
fastcgi_pass unix:/var/run/php/php7.2-fpm.sock;
}
}
Verify if your Nginx configuration file has no error.
# nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
Restart the PHP service.
Restart the Nginx service.
# service php7.2-fpm restart
# service nginx restart
You finished the Nginx integration with PHP on Ubuntu Linux.
3. Configure Nginx Server Blocks
Server blocks is a feature that allows one Nginx server to offer multiple websites using the same IP address.
Lets’ create the necessary infrastructure to use the Nginx Server blocks feature.
# mkdir /websites/mining-pool -p
# cd /websites/mining-pool
# mkdir www
# chown www-data.www-data /websites -R
Our website will be named mining-pool.ninja.
The mining-pool.ninja website files should be inside the /websites/mining-pool/www directory.
Alert!
You need to change your configuration files to reflect your website name.
Create a Nginx Virtualhost configuration file to your website.
# vi /etc/nginx/sites-available/mining-pool.conf
Here is the file with our configuration.
server {
listen 80;
listen [::]:80;
root /websites/mining-pool/www;
index index.php index.html index.htm;
server_name mining-pool.ninja;
location / {
try_files $uri $uri/ =404;
}
location ~ .php$ {
include snippets/fastcgi-php.conf;
fastcgi_pass unix:/var/run/php/php7.2-fpm.sock;
}
}
Create a symbolic link to enable the Nginx virtual host configuration.
Restart the Nginx service.
# ln -s /etc/nginx/sites-available/mining-pool.conf /etc/nginx/sites-enabled/
# service nginx restart
You finished the Nginx Server block configuration.
4. Configure The DNS Domain
Access the GODADDY WEBSITE and purchase a DNS domain.
In our example, we purchase the domain named MINING-POOL.NINJA.
You can use any website to purchase a DNS domain, GoDaddy is just my personal choice.
Create a DNS entry pointing your website to the computer running Nginx.
In our example, we created a DNS entry pointing the domain MINING-POOL.NINJA to the IP address 35.163.100.49.
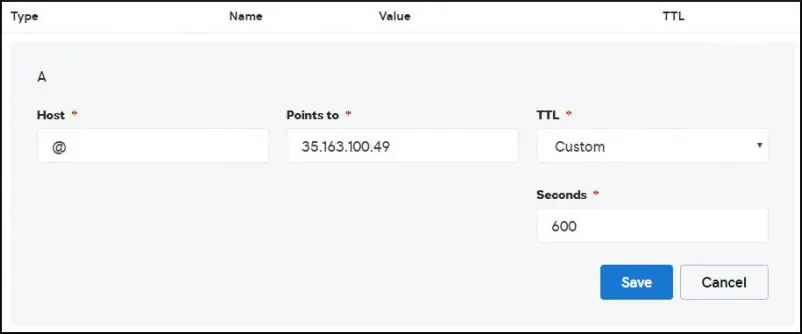
Use the NSLOOKUP command to test your DNS configuration
# apt-get update
# apt-get install dnsutils
# nslookup mining-pool.ninja
Non-authoritative answer:
Name: mining-pool.ninja
Address: 35.163.100.49
You finished the DNS domain configuration.
To test our configuration, let’s create a basic PHP test page.
# vi /websites/mining-pool/www/index.php
Here is the content of the index.php file.
<?php phpinfo(); ?>
Open your browser and try to access the HTTP version of your website.
In our example, the following URL was entered in the Browser:
• http://mining-pool.ninja
The PHP information page should be presented.
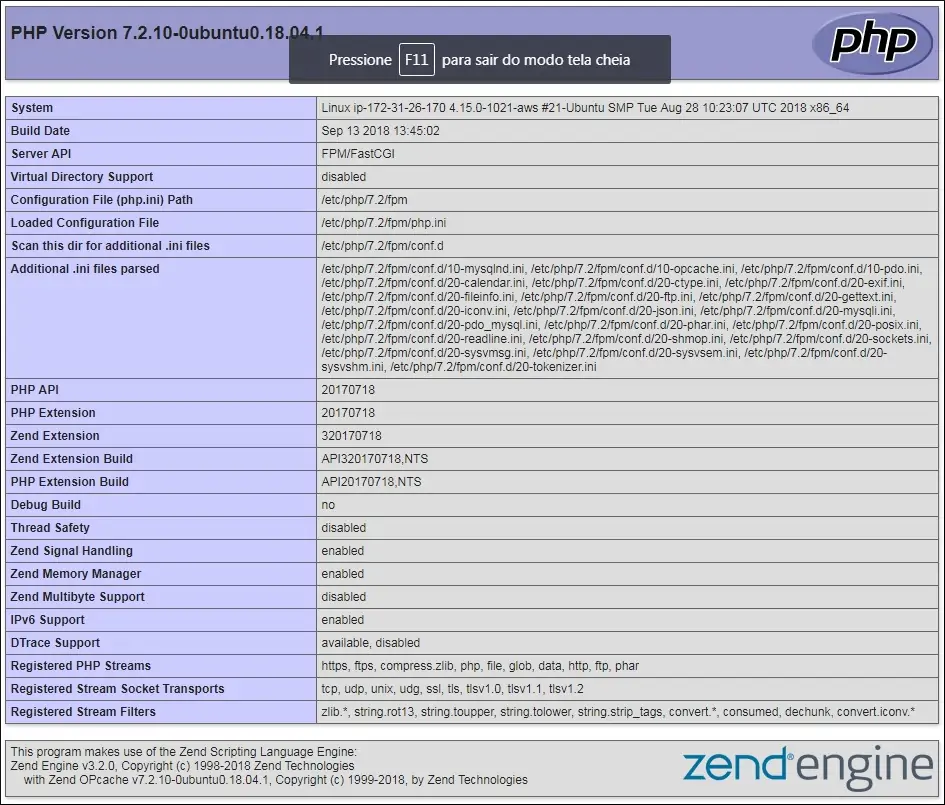
5. Configure The Free HTTPS Certificate on Nginx
Install the required packages to use the LET’S ENCRYPT Free SSL/TLS Certificates on Ubuntu Linux
# apt-get install software-properties-common
# add-apt-repository universe
# add-apt-repository ppa:certbot/certbot
# apt-get update
# apt-get install python-certbot-nginx
Request and install the Nginx free HTTPS certificate.
certbot –nginx -d mining-pool.ninja
• Press (A) to Agree with the Terms of Service.
• Press (Y) to share your e-mail and receive Newsletters.
• Press (2) to automatically redirect your HTTP website to the HTTPS versions.
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator nginx, Installer nginx
Enter email address (used for urgent renewal and security notices) (Enter ‘c’ to
cancel): techexpert.tips@gmail.com
– – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – –
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must
agree in order to register with the ACME server at
https://acme-v02.api.letsencrypt.org/directory
– – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – –
(A)gree/(C)ancel: A
– – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – –
Would you be willing to share your email address with the Electronic Frontier
Foundation, a founding partner of the Let’s Encrypt project and the non-profit
organization that develops Certbot? We’d like to send you email about our work
encrypting the web, EFF news, campaigns, and ways to support digital freedom.
– – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – –
(Y)es/(N)o: Y
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for mining-pool.ninja
Waiting for verification…
Cleaning up challenges
Deploying Certificate to VirtualHost /etc/nginx/sites-enabled/mining-pool.conf
Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access.
– – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – –
1: No redirect – Make no further changes to the webserver configuration.
2: Redirect – Make all requests redirect to secure HTTPS access. Choose this for
new sites, or if you’re confident your site works on HTTPS. You can undo this
change by editing your web server’s configuration.
– – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – –
Select the appropriate number [1-2] then [enter] (press ‘c’ to cancel): 2
Redirecting all traffic on port 80 to ssl in /etc/nginx/sites-enabled/mining-pool.conf
– – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – –
Congratulations! You have successfully enabled https://mining-pool.ninja
You should test your configuration at:
https://www.ssllabs.com/ssltest/analyze.html?d=mining-pool.ninja
– – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – –
IMPORTANT NOTES:
– Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/mining-pool.ninja/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/mining-pool.ninja/privkey.pem
Your cert will expire on 2019-03-31. To obtain a new or tweaked
version of this certificate in the future, simply run certbot again
with the “certonly” option. To non-interactively renew *all* of
your certificates, run “certbot renew”
– Your account credentials have been saved in your Certbot
configuration directory at /etc/letsencrypt. You should make a
secure backup of this folder now. This configuration directory will
also contain certificates and private keys obtained by Certbot so
making regular backups of this folder is ideal.
– If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let’s Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
The system will automatically request the free certificate.
It will also configure your Nginx web server to redirect all HTTP access to the HTTPS version of your website.
In our example, the system modified the Virtualhost configuration file named mining-pool.conf.
Here is the content of the modified file mining-pool.conf.
server {
root /websites/mining-pool/www;
index index.php index.html index.htm;
server_name mining-pool.ninja;
location / {
try_files $uri $uri/ =404;
}
location ~ \.php$ {
include snippets/fastcgi-php.conf;
fastcgi_pass unix:/var/run/php/php7.2-fpm.sock;
}
listen [::]:443 ssl ipv6only=on; # managed by Certbot
listen 443 ssl; # managed by Certbot
ssl_certificate /etc/letsencrypt/live/mining-pool.ninja/fullchain.pem; # managed by Certbot
ssl_certificate_key /etc/letsencrypt/live/mining-pool.ninja/privkey.pem; # managed by Certbot
include /etc/letsencrypt/options-ssl-nginx.conf; # managed by Certbot
ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem; # managed by Certbot
}
server {
if ($host = mining-pool.ninja) {
return 301 https://$host$request_uri;
} # managed by Certbot
listen 80;
listen [::]:80;
server_name mining-pool.ninja;
return 404; # managed by Certbot
}
The KEY file contains your Certificate private key and must be kept in a safe place all the time.
The key file to mining-pool.ninja was stored at /etc/letsencrypt/live/mining-pool.ninja/privkey.pem.
6. Test the Free HTTPS Certificate on Nginx
All the configuration required is done.
It is time to test your configuration.
Open your browser and try to access the HTTP version of your website.
In our example, the following URL was entered in the Browser:
• http://mining-pool.ninja
Nginx will automatically redirect the HTTP request to the HTTPS version of your website.
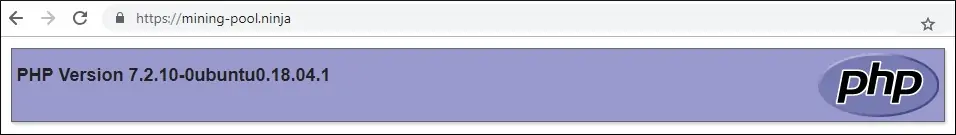
You finished the Nginx HTTPS free certificate configuration.
7. How to Renew The Free HTTPS Certificate
The LET’S ENCRYPT Free SSL/TLS Certificates is valid only for 90 days.
The System creates a scheduled task to automatically renew any certificate within thirty days of expiration.
The scheduled task name is certbot and it is located inside the directory /etc/cron.d.
Here is the content of the /etc/cron.d/certbot file:
# /etc/cron.d/certbot: crontab entries for the certbot package
#
# Upstream recommends attempting renewal twice a day
#
# Eventually, this will be an opportunity to validate certificates
# haven’t been revoked, etc. Renewal will only occur if expiration
# is within 30 days.
#
# Important Note! This cronjob will NOT be executed if you are
# running systemd as your init system. If you are running systemd,
# the cronjob.timer function takes precedence over this cronjob. For
# more details, see the systemd.timer manpage, or use systemctl show
# certbot.timer.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
0 */12 * * * root test -x /usr/bin/certbot -a \! -d /run/systemd/system && perl -e ‘sleep int(rand(43200))’ && certbot -q renew
Use the following command to simulate the process of certificate renew.
# certbot renew –dry-run
You should see the following messages:
Saving debug log to /var/log/letsencrypt/letsencrypt.log
– – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – –
Processing /etc/letsencrypt/renewal/mining-pool.ninja.conf
– – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – –
Cert not due for renewal, but simulating renewal for dry run
Plugins selected: Authenticator nginx, Installer nginx
Renewing an existing certificate
Performing the following challenges:
http-01 challenge for mining-pool.ninja
Waiting for verification…
Cleaning up challenges
– – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – –
new certificate deployed with reload of nginx server; fullchain is
/etc/letsencrypt/live/mining-pool.ninja/fullchain.pem
– – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – –
– – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – –
** DRY RUN: simulating ‘certbot renew’ close to cert expiry
** (The test certificates below have not been saved.)
Congratulations, all renewals succeeded. The following certs have been renewed:
/etc/letsencrypt/live/mining-pool.ninja/fullchain.pem (success)
** DRY RUN: simulating ‘certbot renew’ close to cert expiry
** (The test certificates above have not been saved.)
– – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – –

Leave A Comment
You must be logged in to post a comment.